
Arguably, one of the most important features supported with the release of ESXi 7.0 is the support for vCenter Identity Federation.
Let's take a look at the working philosophy of vCenter Identity Federation, before we get into the details of setting it up.
Multifactor/2-factor authentication (MFA and 2FA) is becoming a very common enterprise cybersecurity practice. It works on the principal of authentication via "Something you know" e.g. Password/pin and "something you have" e.g. One-time-pin/smartcard. The other MFA/2FA very commonly in use today is "something you are" which covers all biometrics method of authentication such as fingerprint/retina scan etc. Not just enterprise security, we are surrounded by MFA even in our personal lives. No payment portal exists today which does not require a password AND an OTP. In addition, you have the option of securing your social media accounts using MFA pin providers such as DUO and Google Authenticator (I would recommend doing this!!).
The intention of VMware with release of Identity Federation was to to make it easy to be secure.
This is why vSphere 7 has Identity Federation. Identity Federation allows us to attach vCenter Server to enterprise identity providers like Active Directory Federation Services (ADFS). This means that vCenter Server participates in the same centralized corporate processes, such as onboarding and termination. It also means that users can use the same methods to log into vCenter Server as they do their desktops and the cloud. This includes MFA & 2FA solutions as well.
Once integrated to the identity provider such as ADFS, the vSphere Client will redirect logins to the provider’s login page. The user or admin logs in using their corporate credentials, including any multifactor authentication that is configured as part of the system. Once they’re authenticated, the identity provider redirects them back to the vSphere Client with a cryptographic token that authorizes them.
Now let's take a looks at the steps required for setting up vSphere Identity Provider using Microsoft AD-FS. I am assuming you already have ADDS,ADCS and ADFS setup in your environment. I have placed all 3 on the same Windows Server VM, however, ideally these must be on 3 different PCs/VMs. In addition ADFS and ADDS must have failover servers as well.
1. On server Manager go to Tools--> ADFS Manager
2. The following window opens, click on Application Groups and select "Add Application Group". In the "Add Application Group Wizard" enter the application group name and select "Server Application Accessing a Web API" and click "Next"

3. Copy the "Client Identifier" to a notepad. You will need this later. Under the "Redirect URls", enter your vCenter Identity provider redirect URIs. To obtain the redirect URls, login to your vCenter server. Go to Administration--> Single Sign-on Configuration-->Click the "i" icon next to "Change Identity Provider" to see the URLs. Enter these URLs and then Click "Next"

4. On "Configure Application Credentials" select "Generate a shared secret". Copy the generated code to your notepad. Click on "Next"

5. In "Configure Web API" enter the "Client Identifier" you would have copied to notepad in STEP3. This is a code exchanged between vCenter and AD-FS, which authenticates the connection. Click "Next"

6. On the "Choose Access Control Policy" select the kind of authentication desired by your enterprise or lab. This is what allows us to configure two factor authentication. Since I am setting this up for testing in homelab, I selected "Permit Everyone". Click "Next " after appropriate Control Policy is selected.

7. In "Configure Application Permissions" select the "Permitted Scopes". vCenter uses OID (Open ID) for authenticating Identity Federation users. Hence we select "openid". In addition we select "allatclaims" which provides authorization token to authenticated users. Click "Next" after the selections.

8. Review all the details and click "Next" in "Summary" page. This complete the addition of application group for our vCenter server.

9. Now, we need to set claim rules and corresponding tokens for this application group in order to authorize authenticated users to carry out functions (roles) assigned to them. To do this, select the newly added Application group and click "Properties". Double Click on the "Web API"

10. On the Web-API Properties Wizards, go to "Issuance Transform Rules" tab and click on "Add Rule"

11. On the "Select Rule template" wizard Select "Send LDAP Attribute Claims" and then click "Next"

12. On "Configure Rule " Enter Claim rule as "Group Claim", Select attribute store as "Active Directory". Under "Mapping of LDAP attributes to outgoing claim types", Select "Ldap Attributes" as "Token-Groups-Qualified by Long Domain Name". Select "Outgoing claim type" as "Group"

13. We need to create two more claim rules. Follow the steps outlined in the screenshots below to configure "Subject Claim" and "UPN Claim"; using the "Add rule" button.

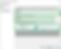
14. After adding all the claim rules, you should be able to see the following rules in the "Issuance Transform Rules" tab of "Web API Properties" Click "Apply" and then "OK" after all rules are configured

15. We are done with ADFS configuration. You can close the ADFS manager window. Open PowerShell in administrator mode and enter the following command:
GET-adfsendpoint | select FullUrlOn the output obtained, scroll down to the url containing "Open-id Configuration". Copy this entire URL to your notepad, we will be needing this later.

16. Now, Login to your vCenter server and go to Administration-->Single-Signon-->Configuration. Click on "Change Identity Provider" on right hand side.

17. The 'Configure Main Identity Provider" wizard open. Select "Microsoft AD-FS" and click "Next"

18. On "ADFS Server" configuration, enter the ADFS server settings. In "Client Identifier" enter the client identifier you had noted in STEP3. In "Shared Secret" enter the shared secret noted in STEP4. In OpenID address, enter the FullUrl noted in STEP15 from the PowerShell output

19. On "Users and Groups" we enter our domain details. The vCenter uses LDAP/LDAPs to obtain this information from the Domain ADDS. Enter the details as per your Domain ADDS. Enter your ADDS domain admin credentials. My ADDS FQDN is ADDS.VirMyst.Homelab. In the Certificates for LDAP, browse and upload your ROOT CA certificate. This is an important step. Please ensure your Domain ADCS, ADDS, ADFS and VCSA are in time sync. I had few failed attempts due to time synch issues in my lab environment.

20. On "Review" cross check your details and click "Finish". Your VCSA Identity Federation configuration is complete!!

21. Open a new browser window and type in your VCSA FQDN. You will see the appearance of the login page has changed. Enter your AD domain admin credentials and click "Next"

22. You will be redirected to your Enterprise ADFS login page . I am using the default ADFS OAUTH login page, this can be customized. Enter the domain admin and password credentials and click sign in.

23. Now, if your ADFS is configured for MFA authentication, this integration provides us means to utilize the same organization (OU) MFA for authenticating vCenter access. After successfully entering the login credentials, you will be redirected to vcenter homepage

Happy testing!!
References:
